WISP PROJELERİ & YAYINLARI VE VERİLER
* WISP hakkında genel bilgilerin yer aldığı sayfaya ulaşmak için tıklayınız.
TUBITAK 215E225 NOLU PROJE
Proje Başlığı: Pasif RFID Etiketlerinde İletişim Güvenliğinin Arttırılması
Proje Amacı : Pasif RFID etiketlerinden olan WISP donanımı üzerinde mevcut güvenlik yöntemlerinin geliştirilerek iletişimde güvenliğin arttırılmasıdır.
YAYINLAR (Yayınları görüntülemek için yayın başlıklarına tıklayınız)
- Aydın Ö., Dalkılıç G. "A Hybrid Random Number Generator For Lightweight Cryptosystems: Xorshiftlplus", 3rd International Conference on Engineering Technology and Applied Sciences Congress (ICETAS 2018), July 17-21, 2018 , Skopje, Macedonia, pp. 46-48.
- Kösemen C., Dalkılıç G., Aydın Ö. " Genetic Programming Based Pseudorandom Number Generator For Wireless Identification and Sensing Platform ", Turkish Journal of Electrical Engineering & Computer Sciences ( Yayın için kabul edildi. , Kabul Tarihi : 29 Nisan 2018 )
- Kösemen C., Dalkılıç G., " Designing a Random Number Generator for Secure Communication with WISP ", 2017 International Conference On Computing and Data Analysis (ICCDA 2017), 19-23 May 2017, Lakeland, Florida, USA, pp. 289-292. DOI:10.1145/3093241.3093285
- Dalkılıç G., " Radyo Frekansı İle Tanımlama Etiketleri İçin Gerçek Rastgele Sayı Tabanlı Üreteç ", Dokuz Eylül University Faculty of Engineering Journal Of Science and Engineering, 18 (54/3), (2016), pp. 640-651. DOI: 10.21205/deufmd.2016185427
PROJE DETAYLARI ve BAŞLIKLARI (Görüntülemek için başlıkları tıklayınız.)
- Proje Özeti
- Amaç ve Hedefler
- Konu, Kapsam ve Literatür Özeti
- Özgün Değer
- Yöntem
- İş-Zaman Çizelgesi
- Başarı Kriterleri
SONUÇ RAPORU (Görüntülemek için başlıkları tıklayınız.)
-
1. GİRİŞ
- 1.1 RFID Teknolojisi ve WISP
- 1.2 Rastgele Sayılar
- 1.3 Genetik Programlama
- 1.4 Doğrulama ve Grup Doğrulama Protokolü 2. LİTERATÜR ÖZETİ
- 2.1 RFID ve WISP İle İlgili Çalışmalar
- 2.2 Rastgele Sayı Test Paketleri ile İlgili Çalışmalar
- 2.3 Rastgele Sayı Üreteçleri ile İlgili Çalışmalar
- 2.4 Genetik Programlama ile Rastgele Sayı Üretimi ile İlgili Çalışmalar
- 2.5 Kimlik Doğrulama Protokolleri ile İlgili Çalışmalar 3. GEREÇ VE YÖNTEM
- 3.1 Donanım Kaynaklarından Rastgele Sayı Üretimi
- 3.2 Genetik Programlama ile Rastgele Sayı Üreteci Geliştirilmesi
- 3.2.1 Başlangıç Popülasyonu
- 3.2.2 Genetik Algoritma Adımları
- 3.2.3 Uygunluk Fonksiyonu
- 3.3 Grup Kimlik Doğrulama Protokolü
- 3.3.1 Kayıt Aşaması
- 3.3.2 Kimlik Tespiti Aşaması
- 3.3.3 Doğrulama Aşaması
- 3.3.4 Doğrulama Protokolü WISP Kodu 4. BULGULAR
- 4.1 Donanım Kaynaklarından Elde Edilen Gerçek Rastgele Sayılar
- 4.2 Genetik Algoritma Sonucu
- 4.2.1 Üretilen SRSÜ NIST STS Sonucu
- 4.3 Grup Kimlik Doğrulama Protokolü Güvenlik Analizi 5. SONUÇ
KAYNAKLAR
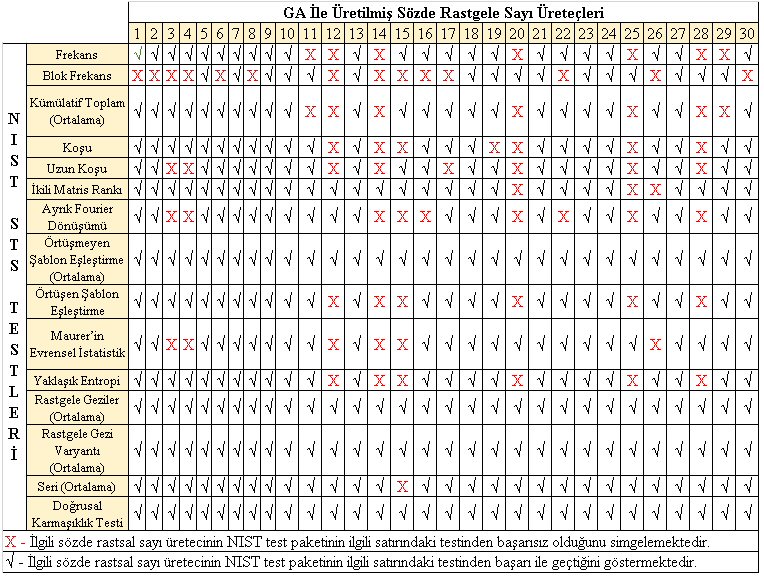
GA İle Üretilmiş 30 Adet Sözde Rastgele Sayı Üreteci ve Üreteçlerin NIST Test Sonuçları
| Nesil(Jenerasyon) Sayısı | Üretim Zamanı | Son Jenerasyon Ortalama Jeton(Token) Sayısı | Çaprazlama Sayısı | NIST Test Sonucu | |
| 1.SRSÜ | 5 | 964722 ms | 28 | 49 | NIST Test Sonucu |
| 2.SRSÜ | 6 | 7021743 | 42 | 49 | NIST Test Sonucu |
| 3.SRSÜ | 6 | 7313761 ms | 40 | 49 | NIST Test Sonucu |
| 4.SRSÜ | 5 | 7038213 ms | 41 | 49 | NIST Test Sonucu |
| 5.SRSÜ | 5 | 10057198 ms | 22 | 49 | NIST Test Sonucu |
| 6.SRSÜ | 7 | 13859593 ms | 27 | 49 | NIST Test Sonucu |
| 7.SRSÜ | 10 | 22446285 ms | 47 | 49 | NIST Test Sonucu |
| 8.SRSÜ | 9 | 20987158 ms | 60 | 49 | NIST Test Sonucu |
| 9.SRSÜ | 11 | 25437796 ms | 54 | 49 | NIST Test Sonucu |
| 10.SRSÜ | 9 | 19303184 ms | 49 | 49 | NIST Test Sonucu |
| 11.SRSÜ | 3 | 5005431 ms | 29 | 49 | NIST Test Sonucu |
| 12.SRSÜ | 5 | 6895103 ms | 25 | 49 | NIST Test Sonucu |
| 13.SRSÜ | 3 | 5199664 ms | 25 | 49 | NIST Test Sonucu |
| 14.SRSÜ | 4 | 6988562 ms | 25 | 49 | NIST Test Sonucu |
| 15.SRSÜ | 3 | 5138736 ms | 27 | 49 | NIST Test Sonucu |
| 16.SRSÜ | 4 | 7171769 ms | 34 | 49 | NIST Test Sonucu |
| 17.SRSÜ | 6 | 7293231 ms | 31 | 49 | NIST Test Sonucu |
| 18.SRSÜ | 4 | 7023424 ms | 37 | 49 | NIST Test Sonucu |
| 19.SRSÜ | 4 | 6634589 ms | 32 | 49 | NIST Test Sonucu |
| 20.SRSÜ | 7 | 12257815 ms | 38 | 49 | NIST Test Sonucu |
| 21.SRSÜ | 3 | 4732673 ms | 23 | 49 | NIST Test Sonucu |
| 22.SRSÜ | 3 | 4823904 ms | 28 | 49 | NIST Test Sonucu |
| 23.SRSÜ | 3 | 4923051 ms | 25 | 49 | NIST Test Sonucu |
| 24.SRSÜ | 4 | 6876360 ms | 28 | 49 | NIST Test Sonucu |
| 25.SRSÜ | 3 | 5157252 ms | 28 | 49 | NIST Test Sonucu |
| 26.SRSÜ | 4 | 7086106 ms | 28 | 49 | NIST Test Sonucu |
| 27.SRSÜ | 4 | 7243786 ms | 36 | 49 | NIST Test Sonucu |
| 28.SRSÜ | 6 | 10844778 ms | 42 | 49 | NIST Test Sonucu |
| 29.SRSÜ | 3 | 5098134 ms | 28 | 49 | NIST Test Sonucu |
| 30.SRSÜ | 4 | 5774462 ms | 24 | 49 | NIST Test Sonucu |
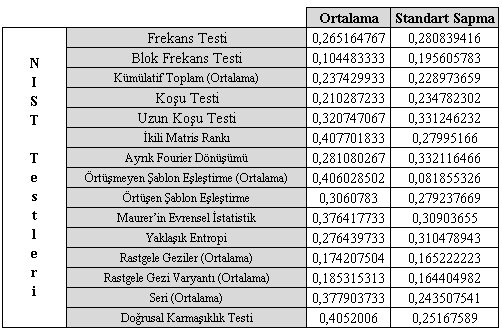
GA İle Üretilmiş 30 Adet Sözde Rastgele Sayı Üretecinin Nist Test Sonuçları Değerlendirmesi
PROJE KAPSAMINDA SEÇİLEN SRSÜ 'nün TEST SONUÇLARI
- Genetik Algoritma Kullanılarak Üretilen Sözderastsal Sayı Üretecinin ENT Test Sonuçları
- Genetik Algoritma Kullanılarak Üretilen Sözderastsal Sayı Üretecinin Diehard Test Sonuçları
- Genetik Algoritma Kullanılarak Üretilen Sözderastsal Sayı Üretecinin NİST Test Sonuçları
WISP ÜZERİNDEKİ KAYNAKLARDAN ELDE EDİLEN RASTGELE SAYILAR (500000 adet sayı örneği paylaşılmıştır.)
1- İVMEÖLÇER ** Dosyayı indirmek için tıklayınız. **
2- SICAKLIK SENSÖRÜ ** Dosyayı indirmek için tıklayınız. **
3- ADC ÜZERİNDEN ÖRNEKLEME ** Dosyayı indirmek için tıklayınız. **
1- DCO-VLO FREKANS FARKI ** Dosyayı indirmek için tıklayınız. **
WISP ÜZERİNDEKİ KAYNAKLARDAN ELDE EDİLEN RASTGELE SAYILARIN NIST TEST SONUÇLARI
1- İVMEÖLÇER ** Dosyayı indirmek için tıklayınız. **
2- SICAKLIK SENSÖRÜ ** Dosyayı indirmek için tıklayınız. **
3- ADC ÜZERİNDEN ÖRNEKLEME ** Dosyayı indirmek için tıklayınız. **
1- DCO-VLO FREKANS FARKI ** Dosyayı indirmek için tıklayınız. **